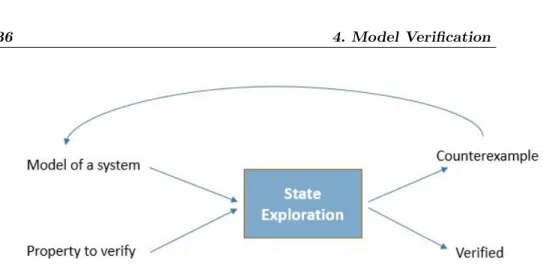
Model Checking Cyber-Physical Systems
Testo completo
Figura


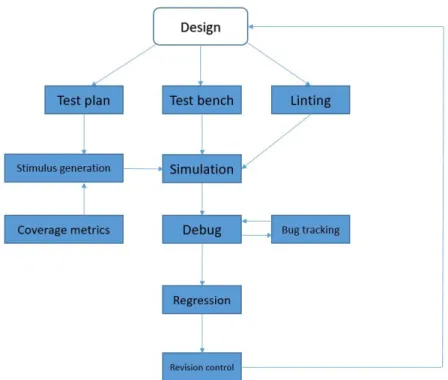

Documenti correlati
Since the publication of her seminal book Jurassic Management (1997) up to her recent works on School Academies, distributed leadership and the New Labour educational
Rarely these disease are managed in the emergency setting, because are often diagnosed by urologists and the overall survival is about 34 months for the UTUC itself; the
The positivity rate and the larval density per gram (number of larvae per g of examined tissue), both at muscle and visceral level, when present, were calculated;
Risk factors for graft survival after liver transplantation from donation after cardiac death donors: an analysis of OPTN/UNOS data.. Lee KW, Simpkins CE, Montgomery RA,
In order to quantify heat impact on ED activity during days with exposure above the threshold, we calculated the average and the max- imum daily number of high-priority
Michele Barbato, Presidente Consiglio dell’Ordine degli Avvocati di Vallo della Lucania Avv.. Nunzio Luciano, Presidente
In this project, we attempt to extend this porting process to other vital parts of the QE code such as the Conjugate Gradient (CG) solver, Γ-point calcula- tions, etc., This