Chapter 1
Introduction
1.1 Homeland Security Concept
Homeland security concerns security efforts to protect Nations against terrorist activity. The term arose following a reorganization of many U.S. government agencies in 2003 to form the United States Department of Homeland Security after the September 11 attacks.
Homeland security is officially defined by the National Strategy for Homeland Security as
"a concerted national effort to prevent terrorist attacks within the United States, reduce America's vulnerability to terrorism, and minimize the damage and recover from attacks that do occur"[1]
The aim of Homeland Security includes[1]:
• Emergency preparedness and response (for both terrorism and natural disasters), including volunteer medical, police, emergency management
• Domestic and International intelligence activities
An Homeland Security approach forces to adopt a new model of cooperation and interconnection between different infrastructures.
The modern society is based on critical infrastructures as: transportation systems (i.e. air and naval transports ), hospitals, schools and Universities, electric power distribution system, telecommunication systems ( i.e. radio and television network, Internet ), databases, etc. In the past this infrastructures were disconnected both physically and logistically. Nowadays, Information Technology can help to mitigate risks and protect these critical systems [4]. The interdependencies between different types of infrastructures is one key aspect which makes protecting these systems a complicated task. For example, information infrastructures depend on electrical infrastructures and vice-versa, and the same relationship holds between communication and transport systems [2]. The solution to this challenging task is an heterogeneous architecture based on information exchanges between different sensors that are managed by one or more central units. This architecture is named as Network Centric Protection Support NCPS. The NCPS carries out a migration of independent systems towards a set of cooperative systems. The concept of Network Centric has been widely viewed as a network of nodes: a set of nodes (consisting of people, devices, information and services) interact using a communications network to optimise the use of resources[3]. This concept can be applied to various domains, such as commerce, education and military operations. Hence an Homeland Security (HLS) System deals with a network of cooperative subsystems[3]. Regarding surveillance systems a typical HLS architecture is shown in Figure 1.1.
The remote nodes, or Remote Sensor Sites (RSS), provides data to intermediate nodes named Area Control Centres (ACCs). The RSS is a manned or unmanned radio station under control of one ACC. Moreover, the remote node is equipped by a sensor for monitoring purpose and network interfaces to share information with the ACC.
The ACC is designed to control a specific geographical area and has to perform the following main tasks:
• Monitor of all risk situations in the surveillance area
• Provide real-time information about the state of targets to the Main Control Center (MCC)
The Main Control Centre handles all ACC data in order to control all the activities into the ACC areas.
The main tasks that MCC has to perform are:
• Real time communication with ACCs
• Data fusion from multiple ACCs
• Provide a synthetic video image in order to understand the risks and to prevent attacks
1.2 Examples of HLS systems
In order to identify the main characteristics of a HLS system we present three examples of systems for different scenarios.
1.2.1Alliance Ground Surveillance (AGS) system
The AGS system consists of a radar-equipped aircraft, Operation and Control stations, datalinks and ground stations to perform persistent surveillance over wide areas from high-altitude, long-endurance, unmanned air platforms operating at considerable stand-off distances and in any weather or light condition [5]. Using advanced radar sensors, the AGS detects and tracks moving objects throughout the observed areas, as well as provides radar imagery of areas and stationary objects.
The advanced radar system TCAR (Transatlantic Cooperative AGS Radar) forms the heart of the system.
The TCAR concept is based on a modular, scalable and open system architecture. The modularity and scalability ensure the adaptation to various aircraft platforms.
The radar is characterized by:
• long processed range,
• SAR and MTI-functions
• an X-band active electronically scanned array (AESA) antenna
• wide- instantaneous bandwidth
• low antenna side lobes
• COTS (Commercial Off The Shelf) digital signal processing
The AGS Core is an integrated system consisting of an air segment and a ground segment.
The air segment is based on unmanned aerial vehicles (UAV). The UAV will be equipped with ground surveillance radar sensor, and also with wideband data links. The ground segment provides an interface between the AGS Core system and a wide range of Command, Control, Intelligence, Surveillance and Reconnaissance (C2ISR) systems to interconnect with and provide data to operational users.
The primary ground segment component consists of a number of ground stations in different configurations, such as mobile and transportable configurations, which provides data link connectivity, data processing and interfaces for interoperability with C2ISR systems.
It should be noted that the interoperability between different sensors is a key point of this system as well as the modularity and scalability of the architecture.
1.2.2 Multi-Modal Netted Sensor Fence for Homeland Security
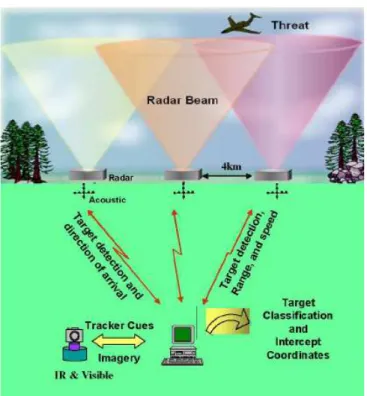
A low cost HLS system solution is presented in [5]. A multi-modal mix of various low cost, low power, netted sensors including unsophisticated radar, acoustic and optical (Infrared and visible) cameras forms the system.
The system and associated sensors is designed to be low cost, low power, and highly portable. A conceptual illustration of the system is shown in Figure 1.3.
The primary detection component in the system is a radar fence. The radar fence is designed to detect approaching targets and provide a cue to the acoustic and infrared sensors that perform the discrimination task. The radar fence consists of multiple remote nodes. Each remote node is a low power (10 Watts), non-scanning (for low cost and complexity), UHF, pulse-Doppler radar (Figure 1.3).
Acoustic microphone arrays are used as the second sensor modality in the system to detect broadband acoustic emissions from approaching targets.
The third sensor modality in the fence is an optical system which is cued by the radar and/or acoustic sensors and slews in angle to acquire, track and identify the potential airborne threat.
Key elements of this system are:
• Modularity
• Easy to transport
• Low cost
1.2.3CENTURION
Centurion is a maritime surveillance system developed by Northrop Grumman[6]. a Maritime Force Protection and Harbour Surveillance system development that is targeted against both surface and underwater threats.
Figure 1.4 illustrates the main functional components and data transfer that form the Centurion architecture. The sensor types that were chosen for a total surveillance capability are acoustic sensors, radars, optical sensors, and an Automatic Identification System (AIS).
To address the underwater threat, two acoustic sensor types are considered: 1. a harbor bottom passive tripwire,
2. water column acoustic sensors.
The harbour bottom passive tripwire consists of line arrays of acoustic hydrophones that are laid on the harbour bottom, usually along straight lines.
Each COTS sensor has its own processor which provides detection and tracking functions. The common interface converts the data from the sensor into a common data structure used by the Sensor Fusion Processor and Contact Manager.
The Sensor Fusion Processor receives the information from the different sensors, correlates all sensors contacts, and provides track management and automated rule-based decisions about whether a target is or is not a potential threat.
For a potential threat, an alert is sounded on the situation display, and relevant potential threat information is transferred to the Command, Control, Communication, Computers, Intelligence (C4I) system.
Centurion is highly scalable. It can be deployed as a minimal standalone system or used as a subsystem which will interface with existing port defence system.
Figure 1.4 Centurion Architecture
As shown the Centurion architecture integrates both the subsurface acoustic sensors and the surface non-acoustic sensors, provides contact data to command and control networks. The primary functions of Centurion are a common sensor data interface, fusion and correlation of multi-sensor systems.
1.3 Definition of HLS features
From previous paragraphs we can conclude that the definition of an HLS system mainly depends on:
1. A scenario definition 2. Threats Identification
Considering the above two points the HLS features may be classified in:
1. Net-centric architecture 2. HLS network topology
3. Remote note architecture ( i.e. the RRS node in Figure 1.1 )
At the beginning of the study the considered scenario was relative to maritime surveillance. The identified targets were classified in small metal ships, fishing vessels, patrol vessels and other similar vessels.
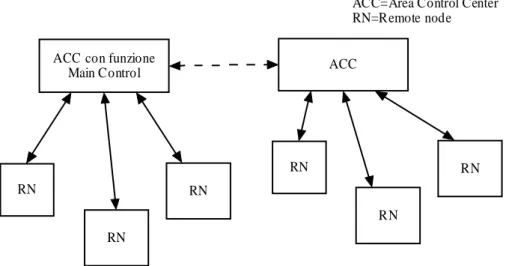
Figure 1.5 shows the architecture for the considered HLS system. In this configuration a local area subsystem including two ACC and some Remote Nodes (RN) is presented. One of the two ACCs can also provide the MCC functionality.
The RN provides detection and tracking functions to the ACCs. The first level of data fusion is carried out in the ACC. The ACC sends data to the MCC that takes decisions about whether a target is or is not a potential threat. Moreover, the MCC generates command controls to manage ACCs and RNs.
The network topology is the layout pattern of interconnections of the various elements of network. In this case, a tree network between ACC and RNs is presented. Instead, a
The Remote Node has to monitor the surveillance area trough different sensors as radar, infrared camera, sonar etc. Moreover, the RN should have different interfaces in order to communicate to other RNs and ACC, and to exploit data coming from GDMSS system or AIS system.
ACC con funzione
Main Control ACC
RN RN RN RN RN RN ACC=Area Control Center RN=Remote node
Figure 1.5 Considered HLS architecture
1.4 Sensor Requirements
A HLS system should have the characteristics of modularity and scalability. In addition, the system should be built using COTS components. As we can see in AGS system the features of HLS system are strictly dependent on the radar sensor capabilities. So, our study will concentrate on the definition of a radar sensor for a HLS system.
The knowledge-base functionality means that the radar must be adaptive with the environment and able to reconfigure itself. As an example the radar may exploit different waveforms depending on a required task without hardware changes, in fact the modularity and scalability may be the features that are involved to the knowledge based functionality. As a matter of fact, both of terms emphasize the ability of the sensor to be flexible and easy to configure.
Nowadays, the Software Defined Radio SDR represents a technology able to satisfy the requirements of reconfigurability and flexibility. The aim of a SDR approach to communication systems is to implement as many of the system functions as possible in software and reconfigurable hardware. While radars made of components for telecommunications may not provide the best performance. An SDR approach to radar design may be useful for prototyping a new radar design. In addition, this approach offers ways of reducing costs, and enabling faster prototyping due to its reconfigurable nature. Radar types which may particularly benefit from the SDR approach are Passive Radars (PR) or Passive Coherent Location (PCL) radars. A Passive Radar is a technology that allows fully functional radar systems to be constructed without the need of a dedicated transmitter. These radar systems operate by exploiting existing transmitters ( i.e. Illuminators of Opportunity) already present within the environment, this significantly reduces system costs. Furthermore, PCL radar systems are able to operate within portions of the radiofrequency and microwave spectrum that have previously been unavailable to radar. Concluding, a SDR approach provides to the Passive Radar the knowledge base functionality and the low cost requirement needed to this work.
This thesis focuses on the adaption of a SDR development platform called GNU Radio, and a device called the USRP, from their original telecommunication function to performing passive radar functions. The adapted versions were tested by implementing a passive radar exploiting digital waveforms.