2 – QoS and Differentiated Services
2.1 - Overview
As explained in the previous chapter, today Quality of Service is a fundamental matter. This chapter aims to give an overview of the various mechanism used together with MPLS to obtain QoS in the scenarios simulated in this thesis.
The treatment reserved to the traffic in order to obtain a certain level of QoS are negotiated between the customer and the network manager and fixed in the Service Level Agreement (SLA). The QoS agreed may regard many parameters, but usually the most important are established to receive particular guarantees as regards the packet loss, delay, jitter and throughput, as we will see in section 2.3.
2.2 – QoS Mechanisms
To obtain a service differentiation, the implementation of proper mechanisms for the traffic treatment is required. The principal functions employed by the routers (figure 2.1) for the traffic treatment proposed by the IETF are [Tofoni, 03]:
• Packet Classification: attends to the identification of the traffic flow of the packet.
• Traffic Control: is involved in all the functions of traffic admission and in the verification of the respect of the SLA. The traffic control functions are four, three fundamental and one optional. All these following functions will be used in the simulations made in this thesis:
o Admission Control algorithm: verifies, after the customer declaration, if is possible to give the QoS required without involving the services given to the other flows.
o Conformity algorithm: is a test to individualize the traffic that is not conforming to the pattern declared by the customer.
o Policer: is the module involved in the treatment of the traffic out of conformity; usual actions are declassing or discarding the exceeding traffic. o Shaper: is an optional module that “shapes” the traffic so that it will respect
an established pattern.
Figure 2.1 – Schematization of a router
• Packet Scheduling: it guarantees the QoS managing the forwarding of packets through particular mechanism of queue managing. Each router has a particular scheduling discipline to decide from time to time which packet of a particular flow
Classification Shaping Policing Input link Output link
Policer: verifies that the input flow is respecting the SLA Classifier: identifies the
traffic flow of the packet
Admission Buffer: accepts or refuses an arriving packet Shaper: operates on the
flows not respecting the established conditions
Congestion Treatment: local organization of the router buffer
Scheduler: chooses the packet to be sent first on the output link
must be transmitted. In the simulations made in this thesis, the algorithm applied is the Weighted Round Robin, explained more in detail in the next chapter.
• Congestion Treatment: is useful to avoid situations of high network congestion; the most used technique is discarding packets when some thresholds are exceeded. A mechanism that is often used is the Random Early Detection (RED). In the simulations made in this thesis, no congestion treatment will be used, because one of the guarantees that we want give to some real time traffic is no packet loss.
2.3 – QoS Parameters
The evaluation of the Quality of Service that a customer receives is fundamentally based on the analysis of the following parameters:
• Delay: It consists on the time passing between the moment in which the data flow is transmitted and the moment in which it is available at the destination. The delay (also called latency) is due not only to the propagation time, but also to the time spent in the queues and the processing time. This parameter is fundamental for the interactive real- time traffic, for the VoIP traffic or the Videoconference, where to establish a good interaction is fundamental that the dialogue has really low delay, good values are lower than 150 ms.
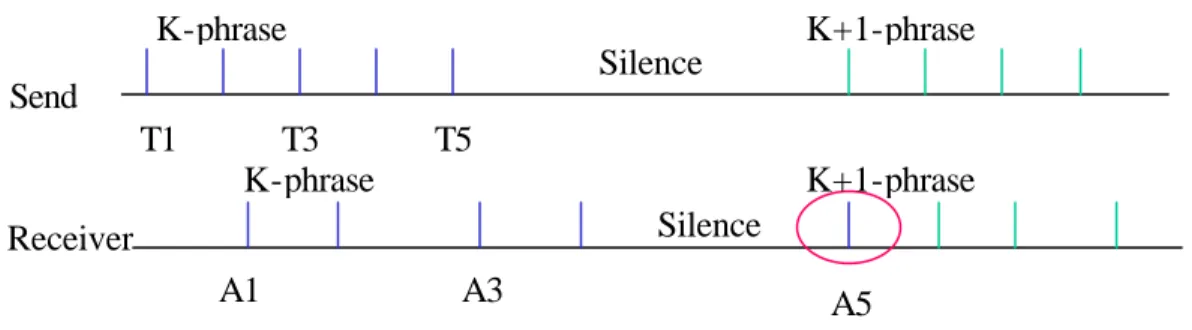
• Jitter: It is the difference in the arrival times of packets. Many times, more than the delay, it is important how much the delay varies from packet to packet. This parameter is especially important for real-time traffic, interactive and streaming (like Video on demand, Radio on line and other). In figure 2.2 is shown the case of two phrases inside a phone call with a small silence between them. If a packet containing the last part of the first phrase arrives with an anomalous delay, it is
times, but there are instantaneous and total limits on the buffer’s ability to smooth out arrival time. The ideal value for the Jitter in the case (treated in the simulations in this thesis) of a VoIP phone call should be less than 30 ms, an empirical value that makes imperceptible jitter to the human ear.
Figure 2.2 – Jitter example for a phone callings
• Packet Loss: The importance of this parameter for the real- time traffic is clear, the real-time traffic uses UDP as transport protocol and UDP has no guarantee as regards the packet delivery. For this reason, every packet lost corresponds to a data loss in the real-time application at the receiver. So, it is very important to guarantee a really low value of packet loss (typically lower than 1% of the total sent) if we want to speak about QoS.
• Throughput: It is the effective rate of data sent obtained by the sender in transmission. This parameter involves not only the real time traffic, but also the TCP traffic, in fact, TCP is rate adaptive and the higher the throughput, the higher is the TCP rate, with the obvious consequence of faster applications (web pages open quickly, Peer-to-Peer applications exchanging more data, and other).
2.4 – DiffServ
The Differentiated Service approach to the QoS requests is very functional, as quickly explained in the introduction chapter, principally because it allocates resources to a small number of traffic classes, but also for its capability to be integrated with other
T1 A1 A3 T3 A5 T5 K-phrase K+1-phrase K-phrase K+1-phrase Silence Silence Send Receiver
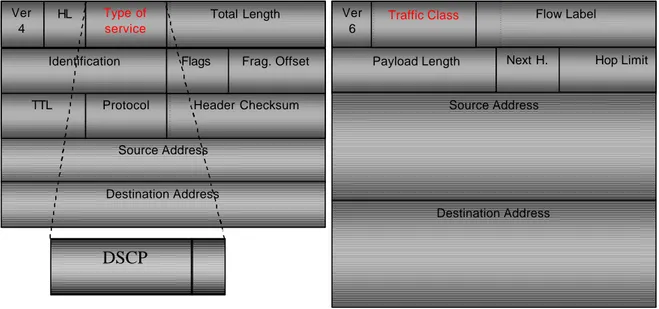
technologies like Traffic Engineering, Constraint based-Routing and especially MPLS. The traffic arriving at the edge router of a DiffServ domain is classified in a certain number of classes, typically two (Best Effort and Premium traffic) or three classes (often called Gold, Silver and Bronze class). The division in classes must be made at the network level; in particular, packets are divided into classes by marking the type of service (ToS) byte in the IPv4 header, or the Traffic Class Octet in the IPv6 header, as shown in figure 2.3. A 6-bit pattern called Differentiated Services Code Point (DSCP) is used to this end in the IPv4 ToS Octet, while in the IPv6, the whole Traffic Class Octet is used [RFC 2474].
Figure 2.3 – IPv4 and IPv6 headers
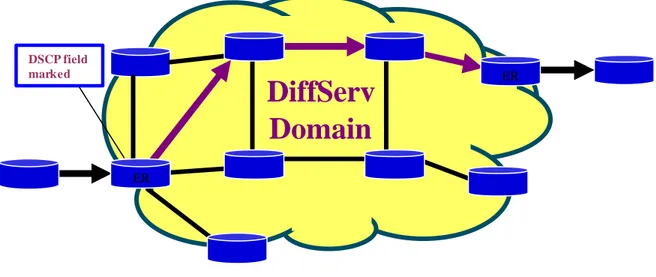
The class assignment is made just one time and only at the edge of the domain, as shown in figure 2.4. Both DiffServ edge routers and the routers inside the domain must be able to apply the appropriate PHB to packets based on the DSCP code point; otherwise unpredictable behaviour may result. In addition, the edge routers may be required to perform traffic conditioning functions as defined by the SLA.
The principal reason to leave the class assignment at the edge routers is to keep simple the network core, avoiding problems of scalability.
Source Address Destination Address Ver 4 Total Length HL Type of service
TTL Protocol Header Checksum Flags
Identification Frag. Offset
Ver 6 Flow Label Hop Limit Next H. Payload Length Traffic Class Source Address Destination Address DSCP
Figure 2.4 – DiffServ domain
Setting the DSCP at one hop and then us ing the value to determine many subsequent hops is a useful thing when supporting DiffServ in an MPLS network [Davie, 00].
At the basis of the DiffServ architecture, there is a particular forwarding treatment called Per Hop Behaviour (PHB). PHB is a description of the externally observable forwarding behaviour of a DiffServ node, so that is the behaviour of individual routers to be defined rather than end-to-end services. The DSCP (or Traffic Class) field is analyzed to find the forwarding treatment to apply to a particular class of service. As described in RFC 2475, the PHB is the means by which a node allocates resources to behaviour aggregates, and it is on top of this basic hop-by-hop resource allocation mechanism that useful differentiated services may be constructed [RFC 2475].
Two main PHB have been standardized:
• Expedited Forwarding (EF): packets marked to receive an EF treatment should be forwarded by the router with the minimal packet loss, low latency, low jitter, assured bandwidth, end-to-end service through DS domains [RFC 2598].
• Assured Forwarding (AF): this behaviour assigns four AF classes. Within each AF class, an IP packet can be assigned to one of three different levels of drop
DiffServ
Domain
ER ER DSCP field markedprecedence in the Weighted Random Early Detection (WRED) scheduling mechanism that should be used [RFC 2597].
In this thesis we will use three traffic classes:
• Gold
• Silver
• Bronze
Each one of them is characterized by different PHB received at every node (MPLS node to be precise), the PHB will not be one of the standard PHB explained previously, because DiffServ will be used not alone, but together with MPLS, Traffic Engineering and Constraint based-Routing. So, the behaviour will be obviously specific (the explanation is postponed to chapter 5). However, like EF, the PHB for the real- time traffic in the first two classes, aims to obtain low delay, low jitter, guaranteed bandwidth and really low packet loss (in the various simulations made in this thesis we have obtained the excellent result of no packet loss, but it is impossible to exclude pathologic cases); in the cases of TCP traffic, the PHB, like AF, aims to assure a certain bandwidth available; the third class real-time and TCP traffic is always treated like best effort traffic with the only difference of following established paths with an assured minimal bandwidth.
2.5 – Class Based Queue (CBQ) and Weighted Round Robin (WRR)
Another peculiarity of the network architecture in this thesis is in the scheduling mechanism using Class Based Queue (CBQ) together with Weighted Round Robin (WRR).
CBQ is a hierarchical method of queuing packets based on their classes or subclasses. A classifier assigns arriving packet to the appropriate class. A class consists of a priority and
speak about output port) bandwidth and a priority is assigned to each class. The bandwidth assignment is flexible because it allows one class to borrow the unused bandwidth from its parent classes. Higher priority flows receive a larger percentage of the available bandwidth.
Each class is assigned to a queue. The scheduler determines the next packet to be sent from the various classes, based on priorities and states of the classes. Weighted-round robin scheduling is used between classes with the same priority [Jaeger, 98].
In the Weighted Round Robin, each queue is serviced in a Round Robin order, one packet at a time. To each queue is assigned a different percentage of the output port bandwidth, and each queue can send only a single packet each time that it is visited. “Weighting” each queue assures the visiting of higher bandwidth queues multiple times in a single service round. In figure 2.5 is represented a case of CBQ/WRR with three classes of service, the first class and the second class allocate the 25% of the output link bandwidth, while the third class allocates 50%. WRR queuing supports this weighted bandwidth allocation by visiting the class 3 queue two times during each service round [Semeria. 01].
Figure 2.5 – CBQ and WRR CLASS 1 25% of the BW CLASS 2 25% of the BW CLASS 3 50% of the BW C1 C3 C2 C3